NetFoundry Platform
Zero trust networking is now composable, programmable software
NetFoundry’s solutions are built on the NetFoundry platform, delivering billions of sessions per year.
Now, you can use the NetFoundry platform to add zero trust connectivity to your products.

Platform Overview
NetFoundry’s solutions are available as turnkey SaaS to securely deliver workloads ranging from AI and APIs to connecting robots, distributed energy and multicloud.
NetFoundry built those solutions on the NetFoundry platform and so do providers. For example, providers use the NetFoundry platform to instantly add zero trust connectivity to their products. This includes ISVs, SaaS, connected product providers, MSPs, IPaaS, cybersecurity providers, IoT solutions and OT technology.
The NetFoundry Platform transforms secure networking and connectivity into composable software, providing components such as overlay networks, identity, authentication, authorization, encryption and microsegmentation as software.
NetFoundry platform
Transform any product into a secure by design product
Zero Trust Native Overlays
Dedicated overlays are provided by NetFoundry or self-hosted, including for on-premises or air-gapped sites. They are software only, zero trust native networks.
The overlays are based on NetFoundry’s Ziti software – NetFoundry open sourced and maintains OpenZiti, the Linux of secure networking.

NetFoundry Ziti Controllers
Controllers enable the management of identities, services, configurations and policies, including authentication and authorization. Controllers include PKI, as a managed service, and support third-party CAs.
NetFoundry Ziti Routers
The routers form programmable, overlay mesh networks, with smart routing and self-healing capabilities.
Routers enable endpoints to make outbound-only connections, without firewall hole punching, NAT or static IP address dependencies. The routers provide telemetry and control and are either hosted by NetFoundry or self-hosted.
NetFoundry Ziti SDKs
Embed zero trust networking directly into applications for agentless zero trust – the zero trust overlay goes anywhere the application goes.
NetFoundry Ziti Tunnelers
Lightweight software, available for every OS, to extend zero trust networking to that device.
NetFoundry Ziti Gateways and Firewalls
Software to extend zero trust networking to sites and clouds. Standalone VMs or containers, and also prebuilt into firewalls, modems, edge servers, API gateways and reverse proxies.
NetFoundry Frontdoor
Agentless approach which identifies, authenticates and authorizes endpoints, while making the server-side unreachable from unauthorized endpoints.
Zero Trust Endpoints
Extend secure by design networking to any application, device or site, including OT, IoT, IT and cloud.

Management and Orchestration
Spin up Zero Trust native overlays in minutes, using NetFoundry’s web console or APIs.

Web console
Centralizes all overlay network management, orchestration and telemetry. White label option available for partners.
APIs
All functions are API-exposed. Leverage via Terraform, Ansible or your IaaS tools. Integrate into your UI or workflow, including for one-time access and just in time (JIT) access.
Telemetry and Reporting
NetFoundry provides identity-based telemetry which links users, devices, services and usage. This includes prebuilt reporting, analytics and audit log, with the option to send to your SIEM.
The first zero trust native overlay networks
NetFoundry is the first to build zero trust into the network with universal identities. Spin up zero trust native overlays, in minutes, for a single AI application or an entire WAN.
Deploy for IT, OT or IoT
Includes agents for Windows, Linux, macOS, iOS, Android, containers, VMs, eBPF daemons. Pre-built into proxies, browsers, modems, edge servers, firewalls. Use SDKs to integrate into any software.
Reliability and performance
NaaS includes HA, dynamic optimization, ingress and egress load balancing, across over 100 PoPs, with 24×7 enterprise support and SLAs. On-premises includes features and tools to get 99.999% uptime.
On-premises, hybrid or NaaS
Deploy in air-gapped sites, OT, multicloud and everything in between. Every overlay is zero trust native with all zero trust functionality built in and prebuilt integrations. NaaS spans over 100 sites.
NetFoundry’s built-in identity (X.509-based) is universal – for workloads, devices, humans. Identity based controls, policy and telemetry replace dependencies on IPs and NAT. Posture and MFA is built-in, as is support for any OAuth or OIDC IDP.
No inbound access
Software-defined, zero trust native overlays makes IT, OT, IoT or AI unreachable from underlay networks. Close all inbound ports and eliminate all VPNs.
Authorize before connect
NetFoundry includes identity, continuous authentication and authorization for users, admins, devices, servers, workloads, AI agents and MCPs. Strong auth is required before overlay access – the overlay itself is auth aware.
Mutual TLS and E2EE
Mutual TLS (mTLS) is built-in for every overlay segment. End to end encryption (E2EE) with keys sovereign to the endpoints means nobody has access to your data. Choose ciphers, including FIPS 140 compliant and libsodium.
JIT, one-time and persistent access
Just-in-time (JIT), one-time and persistent access models, based on authorized identities. Integrated with workflow and ticketing (JIRA, ServiceNow, Zendesk, etc.), or use NetFoundry APIs for your own custom integration.
End to end zero trust
Extend zero trust beyond the firewall to applications or hosts. NetFoundry enabled servers have no listening ports – unreachable from underlay networks – only available to strongly authorized sessions.
Open source foundation
NetFoundry open sourced its core zero trust software into the OpenZiti project, and continues to maintain the project. It is an open core model – only enterprise, government and OEM functions are separate.
FedRamp & Government Cloud
NetFoundry is deployed in FedRamp and Government Cloud environments, as well as on-premises and air-gapped sites. Includes supporting CJIS, HIPAA, PCI and FIPS 140 compliance.
EU CRA
The simplest way to meet EU CRA requirements for connected products. Directly integrate zero trust networking into your product, eliminating VPNs.
NetFoundry Architecture
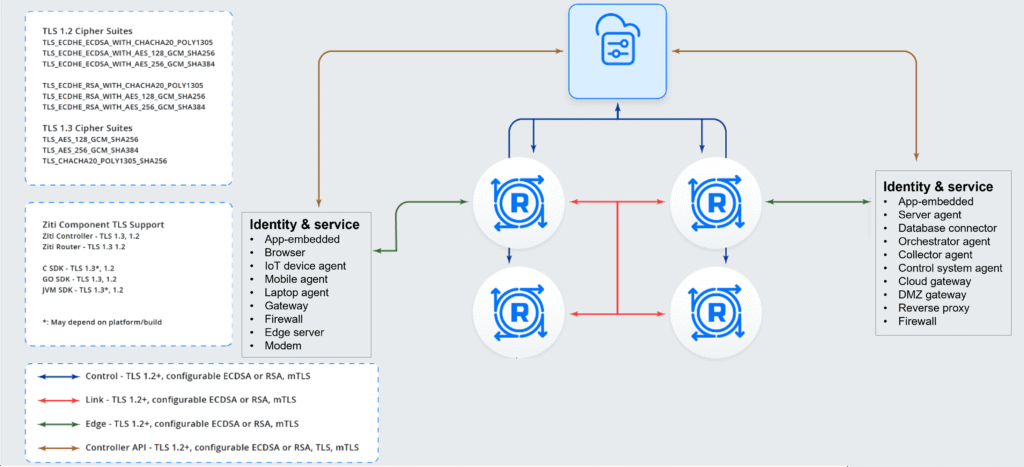
Key components:
- Client-side endpoints. Host endpoints include lightweight software for OT, IoT and IT ‘client side’ devices, available in the Win, Mac, iOS and Android marketplaces.
- Server-side endpoints. Host-based endpoints are available for the ‘server side’, so that connections are controlled end-to-end between client and server.
- Site-level endpoints. Gateways for edges, site and clouds. This includes images in every major cloud marketplace.
- Infrastructure integrated endpoints. NetFoundry endpoints are already built-in to certain browsers, modems, firewalls, edge servers, reverse proxies and API gateways, including Siemens, Caddy, NGINX, Arrow and FreeWave.
- Software integrated endpoints. Use NetFoundry SDKs and APIs to add the endpoints into any software – the software then ships with built-in zero trust connections, without requiring the deployment of endpoints or gateways.
- Clientless access. NetFoundry provides clientless access, with TLS and mTLS options.
- Routers enable endpoints to make outbound-only connections, without firewall hole punching, NAT or static IP address dependencies. The routers are either hosted by NetFoundry or self-hosted.
- Network controllers. Controllers enable the management of identities, services, configurations and policies, including authentication and authorization. Controllers include PKI, as a managed service, and support third-party CAs.
This architecture enables businesses to use “zero trust native” overlays in which all devices and services (internal and supply chain) are strongly identified, authenticated and authorized before any communication, and no network ports are left open for reconnaissance, attack, lateral movement or data exfiltration.
Identity-based authentication & authorization
Every endpoint (user, device, or service) is enrolled via a unique, RSA or EC cryptographic identity (X.509 certificates with optional MFA and IdPs), used for mTLS connectivity. Hardware roots of trust or TSMs can be used for the local storage of each key (PKCS11). This functions as a Proof-of-Possession (PoP) identity such that credential theft is thwarted – the attacker must take control of the human and associated machine to get any access – not simply use stolen credentials, tokens or assertions from the Internet.
Connections are only allowed after verifying identity and posture for both sides of the connection. It is a continuous authentication model – meaning if there is a change in posture or policy during a session, then that session is terminated. Third-party CA, third-party IdP, external JWT, username, password and TOTP are all supported (all RFC 6238 is supported), as primary or secondary auth methods. The CA/PKI solution is included in NetFoundry NaaS, and other CAs are optionally integrated via RFC 7030 support.
All access is explicitly controlled by policies – the default policy is no access. Endpoints and services only do what they are explicitly permitted to do – “positive security model” instead of “negative security model”. This makes it easy for administrators to setup and enforce one-time access, just-in-time (JIT) access and continually authenticated access models. For example, a ticket system or CI/CD workflow can instantly create an identity or policy, and instantly revoke it upon a certain event or timeframe, while continual auth and posture checks mean that state-based events can also instantly terminate the access.
Businesses provision NetFoundry endpoints via standard methods including SCIM and JWT (or build the endpoints into their software so that the network goes anywhere their software goes without agents or gateways).
Because NetFoundry endpoints don’t depend on specialized hardware, and can overlay into existing infrastructure, they often retrofit zero trust security into legacy sites, for example front-ending anything from an OT device to an AS400, or simply enforcing posture and MFA for applications which don’t support mechanisms like SAML, OAuth or OIDC.
End-to-end encryption & data cloaking
All data is secured with strong encryption (configurable ECDSA or RSA for mTLS 1.2+, ChaChar20-Poly 1305, libsodium). In addition, other ciphers such as FIPS-compliant encryption and post-quantum encryption (PQE) are optionally plugged in.
Application data is end-to-end encrypted between the communicating parties – intermediate routers in the overlay cannot read or tamper with the content, and neither can network administrators.
NetFoundry’s encapsulation and encryption helps obfuscate metadata – packets look like TLS traffic on port 443 (or whatever port has been configured in NetFoundry), with no useful info in either content or headers for an adversary to exploit. This level of cloaking helps thwart common reconnaissance (port scanning, protocol fingerprinting, traffic analysis) and reduces actionable intelligence that enemies could gather from the network.
‘Dark’ services, devices or networks
NetFoundry makes services, devices or sites unreachable from unauthorized endpoints:
- When using NetFoundry SDKs, an application, session or service is unreachable from anywhere – it is end-to-end encrypted from the memory space of the application – even hosts don’t have access. This is proof-of-possession (PoP), identity-based microsegmentation, at the session level. For example, an AI agent can be scoped to not have any network access, and not to be accessible from the networks, but to only have access to connect to specifically defined microservices, with NetFoundry providing the mechanisms for identity, authentication, authorization, encryption, policy, delivery and telemetry.
- When using NetFoundry host-based endpoints with host firewalls (or NetFoundry’s integrated firewalls), the endpoint (e.g. a server) can be made to only open sessions outbound to its private NetFoundry overlay and not accept inbound requests from the Internet or underlay network. This is proof-of-possession (PoP), identity-based microsegmentation. A common use case is to make a server (API, application, AI, MCP or web server) unreachable from the Internet or underlay network.
- When using NetFoundry’s edge, site or cloud endpoints, the site devices can be configured to only route outbound sessions to the NetFoundry site endpoint (it functions as the default gateway and network firewall), and to not accept inbound requests from the Internet or underlay network. A common use case is to make an edge site – for example, a site with IoT devices like an energy site or smart building – unreachable from the Internet (instead of relying on a firewall, which is Internet reachable, and therefore extremely vulnerable to attacks). This supports remote access, including one-time, JIT and agentless, as the outbound session from the site devices supports full-duplex connectivity from authorized endpoints.
This overall concept is to shrink the attack surface to insider attacks only – even if an attacker is physically on the same network, they cannot access or even enumerate a NetFoundry-protected resource without being enrolled in the system and authorized for that specific session. NetFoundry secured resources will not respond to any unauthorized ping or connection attempt – the service, device or server might as well not exist.
Microsegmentation and least privilege
Through NetFoundry, administrators define fine-grained segments and access policies, with full visibility from telemetry and audit perspectives (NetFoundry helps discover the network flows and define policies for them).
Each application or device is segmented so they can’t communicate, even if on the same physical network, unless policy specifically allows. The matching of authorized identities to services helps mitigate against malicious lateral movement and data exfiltration.
Every service can function as a ‘network of one’, with authorized endpoints on that virtualized network only able to access the specific service. Likewise, a single device may have access to a service but be completely unable to even see a different service, even if they are on the same physical network. This also sandboxes what a compromised node can do. The ultimate microsegmentation is via the NetFoundry Ziti SDKs which embed zero trust overlay network endpoints into any application or software. As a Golang application:
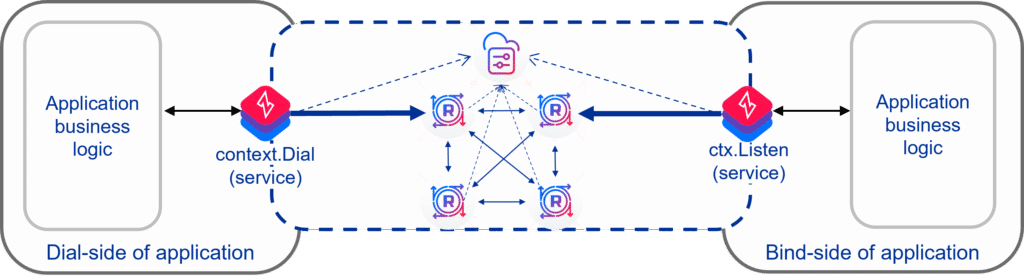
This means the zero trust native network overlay goes anywhere the application goes, without agents or gateways. Since NetFoundry also provides the private overlay as NaaS, operations are massively simplified. The SDK option also provides extreme security – even a compromised host has no access to the session.
Adaptive, HA networking with end-to-end control and visibility
NetFoundry NaaS uses full mesh adaptive routing across over 100 data centers on the world’s top IP backbones to optimize reliability and performance, with options to limit to certain geographies or providers. Each network is private and dedicated to its administrator, who can then decide to add tenants or clients. Overlays can be self-hosted, including in air-gapped sites. This overlay architecture helps NetFoundry provide end-to-end control and telemetry, especially because it can be used for any use case, including supply chain partners.
Overlay network controllers instruct the endpoints and routers on the best performing route for each session. Endpoints simultaneously use different paths for different sessions (no single tunnel backhaul), changing paths as necessary, and doing load balancing. Routers do not have access to the encrypted payloads. Every link is mutual TLS (mTLS).
NetFoundry endpoints leverage diverse transport networks – if a radio link is slow or down, traffic might reroute over a satellite or wired link. The architecture is designed for high availability; there’s no single point of failure, and the system can tolerate outages or route around network damage. This provides resilience in DDIL conditions.
Security policy enforcement is distributed – once endpoints are authenticated and have their session keys, they can often continue communicating through available edge routers even if the central controller is temporarily not reachable.
Both client and server-initiated sessions open outbound towards the overlay. This enables firewalls and servers to deny all inbound. The overlay routers bridge the session.
Universal, secure-by-design networking: summary
NetFoundry is the first to provide a new networking model: secure-by-design networking. The model provides far stronger security, improves reliability and simplifies operations.
As importantly, there are realistic paths towards this north star, with ROI at each step, and businesses choose to use NetFoundry for all use cases or select use cases. NetFoundry helps future proof as well, even including moving off NetFoundry services, if necessary, via its software-only, open source based, API first approach.
The result is virtualized, zero trust native overlays, independent of networking and infrastructure. All sessions (internal and supply chain) are authorized before any communication, and no inbound underlay ports are left open. It includes true end-to-end encryption (the keys remain local to the endpoints), with every link using mTLS. Each overlay delivers authorized, microsegmented sessions, mitigating against data exfiltration. NetFoundry is consumed as cloud native NaaS or self-hosted on-premises, including air gapped. NetFoundry is an all batteries included service, with no external dependencies, but includes prebuilt integrations and APIs for the cases when integrations make sense.
