Blog
Why Every DevOps Engineer Should Be Using Ziti Velocity vs security – why can we not have both? After working in the...
The Power of Dark Services with OpenZiti The recent OpenClaw vulnerabilities sent ripples through the cybersecurity community. Research from the SecurityScorecard STRIKE...
Jarvis or WannaCry, will the real OpenClaw please stand up? OpenClaw (FKA Clawdbot before legal pressure) broke the Internet. And it is...
In an era where digital operations define business success, companies need more than just connectivity—they need secure, controlled, and trusted connectivity. This...
As platform engineers, we are currently stuck between a rock and a hard place. Our internal developers want frictionless access to frontier...
After backpacking Sumatra for 28 grueling days, completely cut off from the rest of civilization, I arrived in Jakarta, Indonesia. There was a...
Simple, secure OT connectivity…without additional installs This may sound like magic, but it is true. Simple, secure OT connectivity, without installing additional...
At DEF CON 33 (Las Vegas, August 7-10, 2025), AmberWolf researchers disclosed critical vulnerabilities in major ZTNA (Zero Trust Network Access) products...
Because both NetFoundry products and OpenZiti software have skyrocketed in popularity (NetFoundry now delivers billions of sessions per month), we are often...
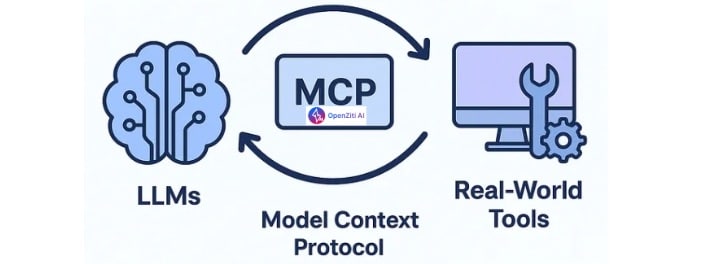
At-Scale AI with MCP for Manufacturing Model Context Protocol (MCP) is rapidly becoming a foundational fabric for industrial AI and agent-based architectures....
At-Scale AI with MCP in Financial Services: Securing Banking and Fintech Workflowswith NetFoundry Model Context Protocol (MCP) is rapidly becoming essential to...
Free Trial Example 2: Securing a Self-Hosted LLM Web UI Example 3: Collaborative AI/ML Development Environment Example 4: Protect Public-Facing AI Application...
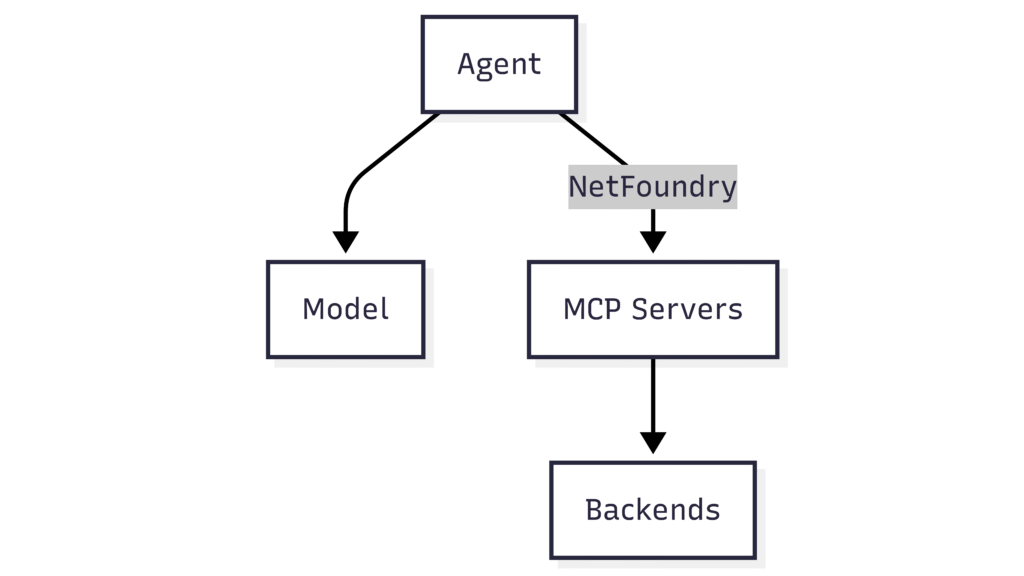
At-scale AI with MCP Model Context Protocol (MCP) is one of the most promising frameworks for at-scale AI. However, like most emerging...