NetFoundry Platform From the developers of OpenZiti
NetFoundry’s Identity-First Connectivity™ is a simple, faster and more secure approach for securing distributed workloads.
- Eliminate 99.99% of exploitation risk by closing all inbound ports.
- Accelerate application deployments.
- Stop wasting time on site-to-site VPNs and never-ending firewall rule changes.
A simpler, more secure alternative to management-intensive firewalls and VPNs
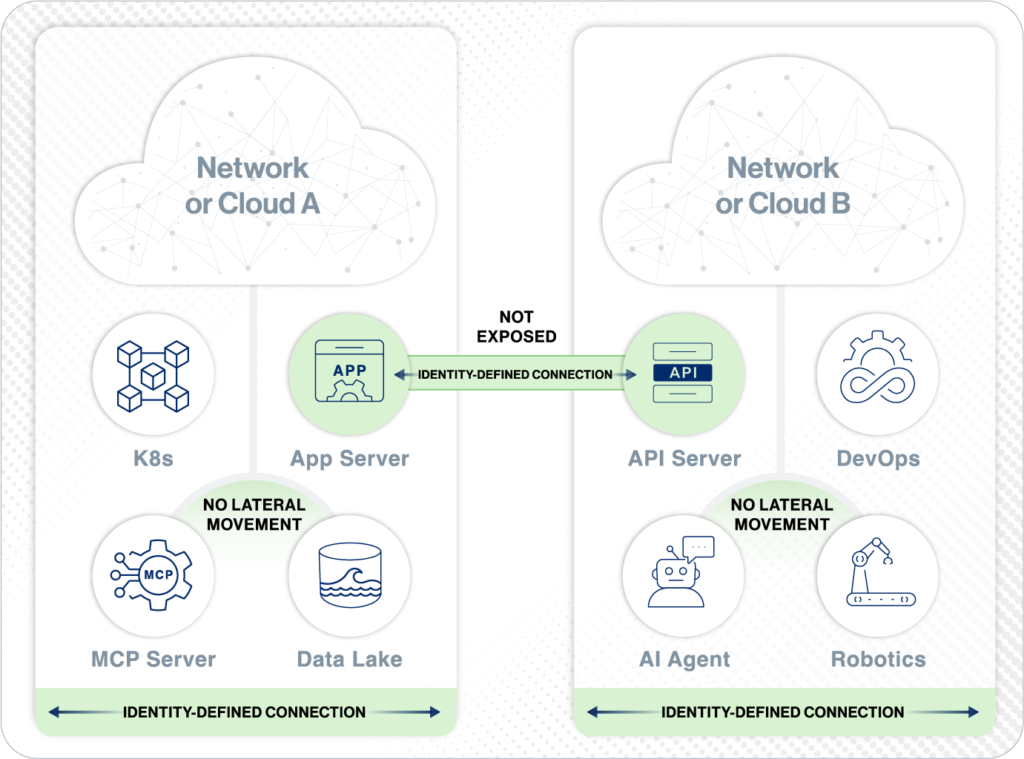
- Authenticate before connect
- No open inbound firewall ports; no network changes required
- Identity-based visibility and control
- Least privilege access by site, host, or application
- Supports any workload—human, machine, or AI agent
Traditional Networks Connect Before Authenticate
- Open inbound ports can be scanned by attackers and weaknesses exploited.
- Management of IPs, firewalls and VPNs is time consuming and visibility is poor.
Identity-First Connectivity™ Authenticate Before Connect
- No open inbound ports—all traffic initiated outbound (port 443 by default).
- Simplified management—no firewall rules to change. Visibility by identity, not IP address.
The Challenges of Traditional Open Networks
- IP addresses make lousy identifiers—they’re too dynamic (DHCP, NAT)
- Attackers can exploit open ports before both authentication and authorization happens.
- Default access is to the entire site, enabling attacker lateral movement.
- New initiatives bogged down by required network and firewall changes.
- Poor visibility and audit—need to aggregate telemetry across devices by IP addresses.
“We sometimes have 15-20 policies/rules across multiple tools, firewalls, and other infrastructure to allow communication between workloads. It takes two weeks to make any change.”
Software-Only Overlay Hides Network Complexity
Simple Zero Trust Workload Connectivity
- Each connection is first reliably authenticated
- No open inbound ports – no network changes required
- Policy defines allowed connectivity
- Fast deployment and updates—no network or firewall changes required
- Full identity-based visibility
- Robust, high performance network fabric
“Segmenting a workload from cloud to on-prem can require dozens of network/security changes and weeks of coordination – whereas an overlay can enable secure connectivity in seconds by updating identity-based policy.”
How Identity-First Connectivity Provides Workload Security
- Authentication with strong identity
- Authorization with Least Privilege
- Granular Scope with Microsegmentation
- Privacy with Full End-to-End Encryption
- One place to get full visibility and audit
Flexibility to Support Any Distributed Environment
Connectors
- Lightweight connectors run on desktops, servers, mobile, IoT devices (Windows, Mac, Linux, Android, iOS)
- Connector embedded directly into app via SDK (Golang, C, JAVA, .Net, Swift or Python)
- Clientless Endpoints using Frontdoor connectivity
Network Fabric
- Hosted by you or NetFoundry
- Private per customer
- 100+ PoPs on all major clouds
- HA and dynamic least-cost routing
- 99.95% uptime SLA, 24x7x365 support
Segmentation
- Least privileged access
- No lateral movement allowed
- Segmentation by site, host, or app
Management & Control
- Comprehensive identity, PKI, integrations, and reporting
- Hosted by you or NetFoundry
- Air-gapped environments supported
- User interface and comprehensive APIs
Fast Deployment, Easy Changes
NetFoundry deploys quickly, and changes are easy due to the independent way each component is managed by policy.
- No network or firewall rule changes required.
- Policies based on identities and services, not ever-changing IP addresses.
- Network-wide visibility by identity, not IP addresses.
- No coordinated setup between entities that need to communicate.
- Every connection to the fabric is independent and identity-verified.
- All connectivity is controlled by policy. Default is to deny all.
Robust Manageability
- Identities and policies (rather than IP addresses) help you establish which elements can see and connect to your workloads, and precisely what they have access to.
- Posture checks and continuous authentication help you insure that connected elements meet your security standards and haven’t been compromised.
- Just-in-time programmatic policy changes apply instantly and can have limited duration.
- And of course there’s the full array of event management, metrics, and integrations that you need from an industrial-strength solution.
Built On The World’s Most-Used Open-Source Software for Zero Trust Connectivity
The team at NetFoundry developed and still maintains OpenZiti—the number one open-source solution for zero trust network connectivity.
OpenZiti underpins the NetFoundry solution. As an open-source project, it is exposed to the scrutiny of developers all over the world. Potential issues are uncovered and addressed immediately for the highest level of confidence.
NetFoundry Deployment Options
Open Ziti
Self-Hosted Open Source
- Community support
- Self-deployed and managed (connectors, routers, controller), self-orchestrated
Self-Hosted
Self-Hosted Licensed
- Enterprise-grade support (24×7)
- Self-deployed and managed (connectors, routers, controller), self-orchestrated
- Operational tooling: Production support tools, backup/restore, platform LCM, SCIM, installers
- Contracted relationship (indemnification)
- FIPS compliant
- Use case and/or implementation documentation
Cloud
SaaS
- Enterprise grade support (24×7)
- Fully managed by NetFoundry (100+ POPs) with 99.95% uptime SLA
- Operational tooling: Production support tools, backup/restore, platform LCM, SCIM, installers
- Contracted relationship (indemnification)
- FIPS compliant
- Use case and/or implementation documentation
- SOC 2 compliant
Simple to deploy, simple to operate, and eliminates 99.99% of exploitation risk
Who Doesn't Love Simple & Secure?
Learn More

NetFoundry White Papers Executive Summary In today’s interconnected digital world, Application Programming Interfaces (APIs) play a crucial role in enabling data exchange and service integration across organizations. As their usage...

NetFoundry Case Studies KEO KEO International Consultants, a global leader in architecture, engineering, and project management, has been at the forefront of delivering iconic projects for over 57 years. Ranked...

NetFoundry White Papers Introduction: The State of the Managed Services Industry As digital transformation reshapes industries, managed service providers (MSPs) are increasingly tasked with securing access across diverse customer environments....

NetFoundry White Papers Zero Trust IoT The Internet of Things (IoT) has transformed both industrial and consumer landscapes by enabling interconnected devices to communicate and share data seamlessly. However, as...
Talk With Us
Learn more about securing workloads with Identity-First Connectivity™
