Securing Critical Infrastructure

Security for Power & Energy Solutions
Are You Ready?
Today’s energy infrastructure is more reliant than ever on connectivity and solutions driving automation and reducing risk. Secure and unhackable energy distribution systems are paramount to ensuring the world can “keep the lights on”. Robust protection of critical infrastructure is mandatory, not an option!
- Electric utilities must comply with the evolving NERC cybersecurity requirements
- Upcoming revisions to NERC’s CIP-003 standard, particularly CIP-003-9, will become effective on April 1, 2026.
These revisions introduce enhanced zero trust controls, focusing on:
- Improving authentication for remote users
- Securing communication with assets containing low-impact Bulk Electric System (BES) Cyber Systems
- Improving visibility into OT systems.
Furthermore, CIP-003-10 and CIP-003-11 propose even more rigorous zero trust requirements, including stronger identity management and authentication protocols. These revisions underscore the need of zero trust principles in securing utility networks.
CIP-003-9/10/11 | NetFoundry Zero Trust Solution |
|---|---|
R1: Cyber Security Policies & Security Control | Scalable, programmable connectivity |
R2: Electronic Access Controls (Least Privilege & SRA) | Least Privilege, E2E encryption |
R2: Vendor Electronic Remote Access | Built-in PKI, AuthZ, AuthN, micro-segmentation |
R2: Secure Transient Cyber Assets & Removable Media | Strong Identities and Posture Checks
|
R2: Incident Response & Logging | Comprehensive events, metrics |
R2: Physical Security & MFA Integration | mTLS and MFA |
R2: Threat Monitoring & Malicious Traffic Detection | Least Privilege Access and continuous AuthN |
R2: Encryption of Authentication Data in Transit | mTLS and Chacha20/Poly1305 |
R3: Delegation & Compliance Reporting | RBAC, APIs and detailed logging |
R4: Documented Policy Implementation & Enforcement | Ease of use drive compliance |
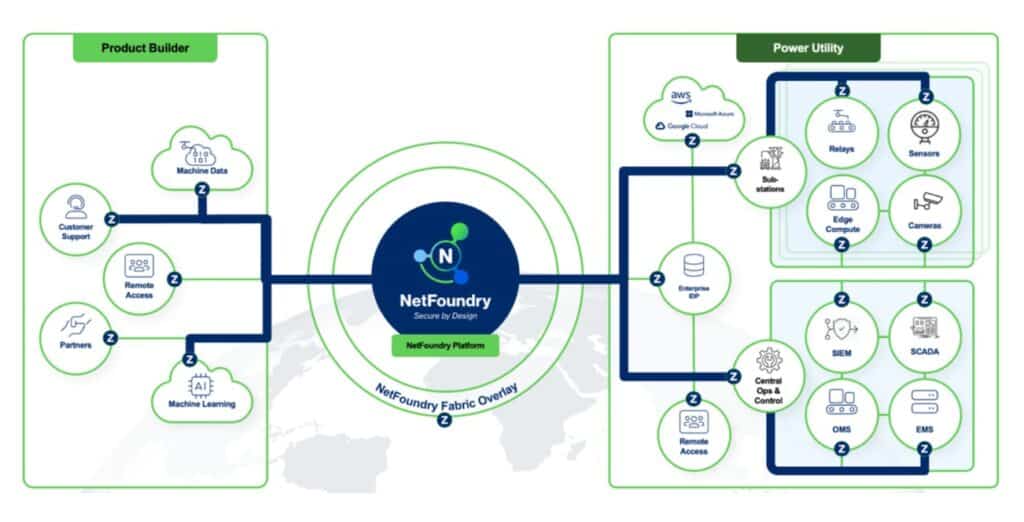
NetFoundry’s Zero Trust Platform offers a comprehensive, easy-to-deploy solution that enables electric utilities to enhance security, simplify compliance, and improve operational efficiency by embedding zero trust connectivity directly into existing applications, devices, and edge compute systems, enabling product makers to rapidly enhance the security of their offerings with minimal disruption. Here’s how NetFoundry can address the most critical challenges faced by utilities in achieving compliance and securing their OT and IT environments
Embedded Solution for Product Makers
NetFoundry’s Zero Trust Platform can be easily embedded into existing applications, devices, and edge compute environments, empowering product manufacturers to quickly integrate zero trust connectivity into their solutions. Whether you are developing IoT devices, edge computing systems, or industrial control systems, NetFoundry provides a seamless, secure framework that ensures your products meet compliance standards while offering robust protection against evolving cyber threats. With NetFoundry, you can accelerate product development timelines, improve security, and simplify the deployment of secure, compliant solutions to your customers.
NetFoundry’s Zero Trust Platform is purpose-built to enable comprehensive connectivity use cases of the electric utilities while adhering to the stringent cybersecurity and regulatory requirements. By embedding zero trust principles into devices and applications, NetFoundry enables granular access control, secure remote connections, network segmentation, and comprehensive audibality. This makes it easier for utilities to comply with NERC’s latest requirements while reducing risk and enhancing overall security posture.
Use Cases | Old Game – VPNs | New Game – NetFoundry |
|---|---|---|
Connectivity and Security | Persistent VPN tunnels with open inbound ports; flat network structure increases risk of lateral movement | Zero Trust, Least Privilege, micro segmented, and no inbound ports – dramatically reducing the attack surface |
Ease of Use and Scale | Complexity/cost grow linearly with each site; maintain and expose IP addresses and device passwords | Deployment and management with intuitive orchestration platform, scaling effortlessly as the network grows |
Secure Remote Access to OT Assets | Multiple logins (VPN, jump server, etc.), fragmented user/role control at each | Frictionless user access with permissions managed once at the hub |
Centralized Access Control | Highly fragmented duplicate, repetitive provisioning at each sub-station. Hard to scale and error prone | Centralized, consistent, micro-segmented access control policies across your deployment.
Integrate with corp IDP
|
Compliance & Auditing | Risk of NERC/CIP non-compliance;
decentralized logs and limited correlation make auditing difficult
| Zero Trust connectivity with centralized auditing enables compliance with NERC-CIP, NIST, CRA, IEC62443 etc. |
Micro-Segmentation | Not supported in VPNs. Additional advanced bolt-on tools required to micro-segment | All connectivity is micro-segmented by design.
No lateral movement possible
|
Hardware Requirements | Dedicated VPN/jump server appliance per site | Software-based & embedded into product – Use
any available existing compute
|
Routing & Performance | Often forced hairpin or single path | Smart Routing improves performance and resilience |
For product makers, NetFoundry offers a streamlined solution to enhance the security of your applications, devices, and edge compute solutions. By integrating NetFoundry’s platform, you can provide
your customers with enhanced security features and help them achieve regulatory compliance with minimal effort.
To learn more about how NetFoundry can help your organization secure its critical infrastructure and simplify compliance with the latest CIP standards, reach out directly to our sales team at
sales@netfoundry.io.