In an era where digital operations define business success, companies need more than just connectivity—they need secure, controlled, and trusted connectivity. This is the vision NetFoundry delivers through its innovative Ziti platform, a zero-trust, identity-centric networking solution used by organizations around the world to secure applications, workloads, and devices without the complexity of traditional security tools.
As businesses scale, so do their digital identities. Every user, device, application, API, or workload becomes part of your trust ecosystem. But maintaining compliance across all these identities can be overwhelming—and a single non-compliant identity can put your business at risk.
This can be addressed by leveraging the NetFoundry APIs in combination with custom code and cloud-native tools to manage identities and automatically trigger actions based on their compliance status.
Okay — let’s see how it works in the real world
Overview
Detect and handle non-compliant Ziti identities effectively to ensure security and policy adherence. Ingest these identities into Cosmos DB or AWS databases for centralized storage and management. Run compliance actions automatically on any changes detected in Cosmos DB by leveraging Azure Functions to maintain up-to-date enforcement and monitoring.
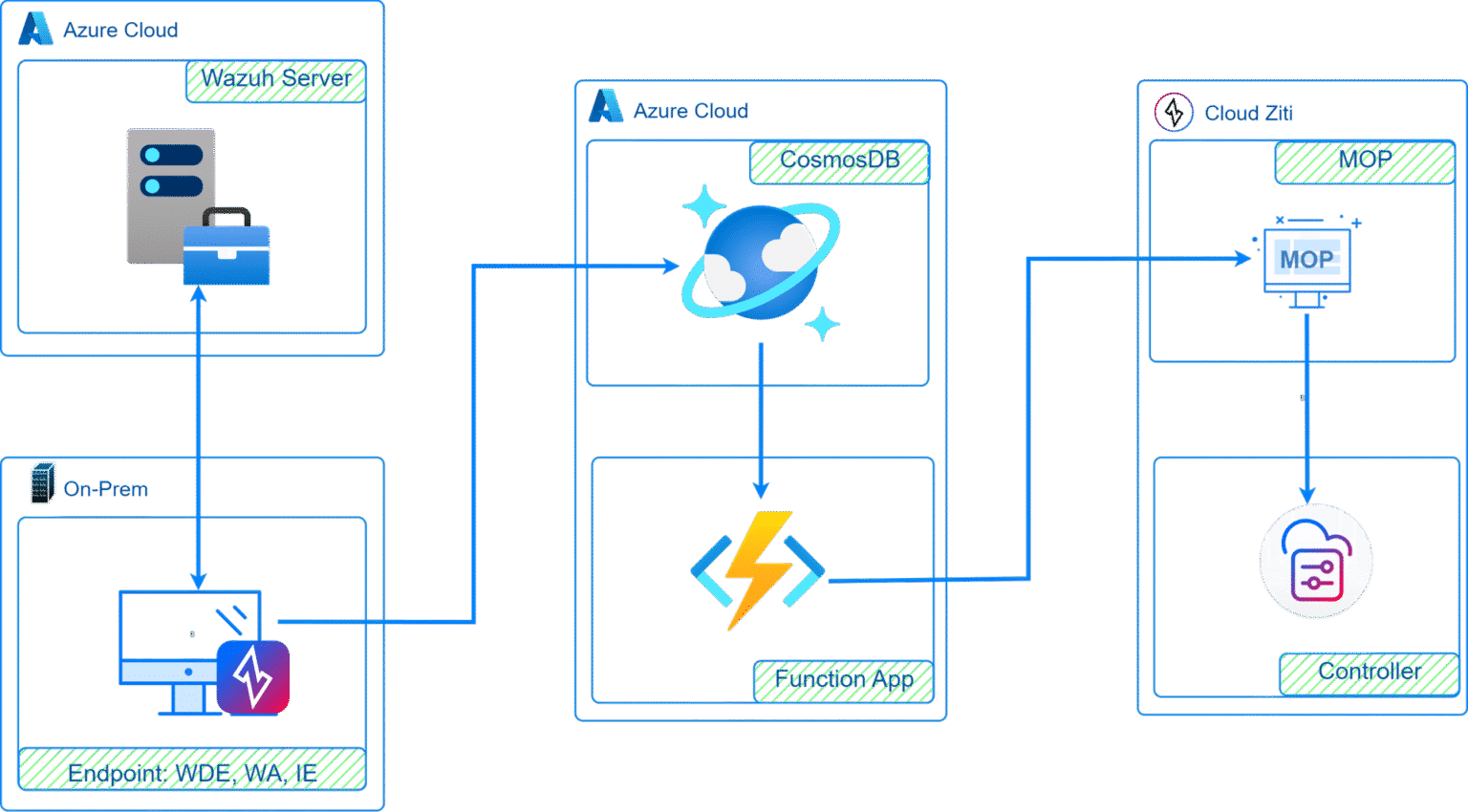
Architecture Overview
- If the Wazuh server (XDR) detects an endpoint as non-compliant, the Wazuh agent on that endpoint executes code.
- When the Wazuh agent runs code, it extracts all identity information from WDE and sends it to CosmosDB for centralized storage.
- A change in CosmosDB triggers an Azure Function app.
- The code runs in a Docker container within the Function app. When triggered, it collects the latest identity information from CosmosDB and sends a POST request to MOP via API to disable the identities.
- Upon receiving the signal, MOP disables the identities on the controller for the specified duration
The result: Stronger security, smoother operations, and greater confidence in every connection your business depends on. It provides a layer of protection that works silently in the background, ensuring your operations stay secure without adding complexity for your teams.
1. Always-On Oversight
Instead of periodic audits or manual reviews, Ziti Compliance Check continuously monitors every identity. This ensures that risk is always minimised, with no dependency on human effort or timing.
2. Immediate Risk Reduction
When a non-compliant identity is detected, the system responds instantly—preventing potential threats from escalating. Identities are automatically disabled until they meet your organization’s standards.
3. Centralized Visibility
Business leaders and IT teams gain a unified, real-time view of compliance across the organization. This improves decision-making, simplifies reporting, and creates transparency across business units.
4. Designed for Modern Cloud Environments
Whether your operations run on AWS, Azure, or hybrid cloud setups, Ziti Compliance Check integrates seamlessly, supporting your digital transformation strategies without disruption.
Why Identity Compliance Is a Business Imperative
Cyber threats have evolved, and so have the expectations of regulators, customers, and partners. A single non-compliant identity can expose an organisation to:
- Costly data breaches
- Interruptions in service delivery
- Brand and reputational damage
- Legal or regulatory penalties
For business leaders, this means compliance isn’t just an IT responsibility—it’s a strategic requirement.
You can leverage the flexibility provided by NetFoundry to bridge this gap by ensuring that every identity interacting with your business systems is trusted, up to date, and fully aligned with your security policies.
The Business Value: What Leaders Gain
Beyond improved security, this approach delivers measurable value across operations and governance.
Reduced Operational Risk
Automated compliance removes blind spots, minimizes identity-related vulnerabilities, and keeps unauthorized access at bay.
Lower Resource Burden
Your teams no longer need to manually track, validate, or deactivate non-compliant identities. Time saved can be redirected toward innovation and high-impact initiatives.
Stronger Regulatory Alignment
By ensuring consistent compliance, organizations stay audit-ready and can prove adherence to security frameworks with confidence.
Enhanced Customer & Partner Trust
Demonstrating robust, automated identity compliance reinforces your commitment to security—strengthening stakeholder relationships and brand credibility.